Phishing Alert: Fake Email Scam Mimics Pitt Passport Login Page
Pitt Information Technology has identified a new email phishing scam targeting University students, faculty, and staff. The scam claims you have a new important message and prompts you to click a link to view it. The link directs you to a webpage that mimics the Pitt Passport login page, which attempts to collect your Pitt username and password. The scam appears to originate from a University email address.
The following is a sample of the recent scam. Note that this scam message may appear in your junk email or quarantined email folder. Always use caution in responding to messages in these folders. If you receive this message (or any message similar to it), please report it as a phishing scam by forwarding the email message as an attachment to phish@pitt.edu. Detailed instructions on reporting scams are available at https://www.technology.pitt.edu/security/phishing-scams.
******************************************************************************
From: Pitt user
Subject: Secure Message
You have 1 New Important Message
Click below to view message details.
<malicious link>
University of Pittsburgh
******************************************************************************
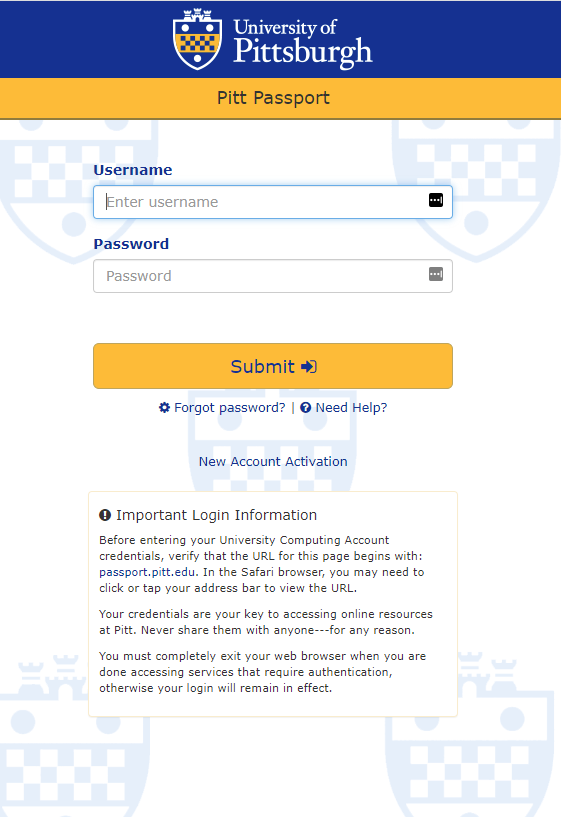
Clicking the link displays a webpage that mimics the Pitt Passport login page:
Pitt IT strongly recommends that you do not reply to unsolicited emails or emails from unverifiable sources. If you were not expecting to receive such an email, confirm with the sender prior to interacting with the message. If you must interact with the message, avoid clicking on links contained in such emails. These may lead to sites that contain malicious software, or sites that attempt to steal your credentials. If a link looks suspicious, you can hover over the link with your mouse to preview the URL without clicking on it.
In addition, Pitt IT recommends that all students, faculty, and staff install Antivirus and Anti-Malware (Malwarebytes) Protection. Departments can submit a help request to obtain Malwarebytes for multiple machines.
Please contact the Technology Help Desk at 412-624-HELP (4357) if you have any questions regarding this announcement.